Configure seu próprio proxy sock5 via openvpn



Responsável: * Coffnix
Descrição
Orientar sobre como utilizar uma VPN com ou sem gateway default, com uso de proxy sock5, para ser utilizado em qualquer aplicação compatível, como web browser, aplicativo telegram e outros.
Requisitos
- Servidor Linux. Neste exemplo estamos utilizando Funtoo Linux, porém pode ser Gentoo, Opensuse ou qualquer outra distro, bastando adaptar os comandos de instalação de pacotes ou compilando os softwares utilizando o código fonte.
- Recomendável usar uma VPS na digital ocean, ou amazon AWS ou Azure, GCP ou OCI, rodando fora do país, preferenciamente EUA.
Configuração
Servidor
Google Authenticator
Compile a lib do google:
root # emerge sys-auth/google-authenticator
Crie o ambiente:
root # groupadd gauth root # useradd -g gauth gauth root # mkdir /etc/openvpn/google-authenticator root # chown gauth:gauth /etc/openvpn/google-authenticator root # chmod 0700 /etc/openvpn/google-authenticator
Script de criação de usuários
Crie um script para criação de usuários do openvpn + google 2FA:
root # touch /usr/sbin/gen-mfa.sh ; chmod +x /usr/sbin/gen-mfa.sh ; vi /usr/sbin/gen-mfa.sh
/usr/sbin/gen-mfa.sh - script para criação de usuáriosMFA_LABEL='OpenVPN Server'
MFA_USER=gauth
MFA_DIR=/etc/openvpn/google-authenticator
user_id=$1
if [ "$user_id" == "" ]; then
echo "ERROR: No user id provided to generate MFA token"
exit 1
fi
useradd -M -c "$user_id" -s /sbin/false "$user_id"
passwd "$user_id"
echo "INFO: Generating MFA Token"
su -c "google-authenticator -t -d -r3 -R30 -W -f -l \"${MFA_LABEL}\" -s /etc/openvpn/google-authenticator/$user_id" - gauth
PAM + 2FA Google Auth
Crie o arquivo de configuração do pam:
root # vi /etc/pam.d/openvpn
/etc/pam.d/openvpn auth [user_unknown=ignore success=ok ignore=ignore default=bad] pam_securetty.so
auth required /lib64/security/pam_google_authenticator.so secret=/etc/openvpn/google-authenticator/${USER} user=gauth forward_pass
auth include system-auth
account include system-auth
password include system-auth
Integração do PAM com LDAP + MFA (opcional)
Configure o /etc/pam.d/openvpn da seguinte forma caso já possua uma base LDAP ativa e integrada com o PAM:
/etc/pam.d/openvpn - Integração do PAM com LDAP + MFA#%PAM-1.0
auth required /usr/local/lib/security/pam_google_authenticator.so secret=/etc/openvpn/google-authenticator/${USER} user=gauth forward_pass
auth required pam_ldap.so config=/etc/openvpn/auth/testemfa.conf use_first_pass debug
account sufficient pam_permit.so
E configure o arquivo de autenticação na base LDAP /etc/openvpn/auth/testemfa.conf:
/etc/openvpn/auth/testemfa.conf host 127.0.0.1
base dc=hackstore
pam_filter objectclass=posixAccount
pam_login_attribute uid
pam_member_attribute memberuid
pam_crypt local
ssl no
Configure também o arquivo /etc/ldap.conf:
/etc/ldap.conf uri ldap://localhost/
base dc=hackstore
ldap_version 3
ssl start_tls
tls_checkpeer no
binddn cn=ldapadmin,dc=hackstore
bindpw senha@senha
OBS: Não se esqueça de compilar o PAM com suporte a LDAP, e realizar a configuração dos restantes dos arquivos do PAM.
=Servidor
Servidor OpenVPN
Compile o openvpn:
root # echo 'net-vpn/openvpn down-root examples iproute2 lzo pam pkcs11 plugins ssl -inotify -libressl -lz4 -mbedtls -selinux -static -systemd -test' >> /etc/portage/package.use root # emerge net-vpn/openvpn
Crie as chaves e certificados
root # cp -rp /usr/share/easy-rsa /etc/openvpn/keys root # cd /etc/openvpn/keys
Siga este artigo, respeitando o diretório original /etc/openvpn/keys:
https://wiki.gentoo.org/wiki/Create_a_Public_Key_Infrastructure_Using_the_easy-rsa_Scripts
Configuração
Crie o arquivo de configuração do servidor:
root # vi /etc/openvpn/openvpn.conf
/etc/openvpn/openvpn.conf port 1194
proto udp
dev tun0
ca /etc/openvpn/keys/pki/ca.crt
cert /etc/openvpn/keys/pki/issued/FuntooHost.crt
key /etc/openvpn/keys/pki/private/FuntooHost.key
dh /etc/openvpn/keys/pki/dh.pem
server 10.100.0.0 255.255.255.0
persist-key
persist-tun
ifconfig-pool-persist ipp.txt
keepalive 10 120
comp-lzo
user nobody
group nobody
status openvpn-status.log
log /var/log/openvpn.log
verb 4
# PAM + 2FA Google Aut
plugin /usr/lib64/openvpn/plugins/openvpn-plugin-auth-pam.so openvpn
Cliente
Cliente OpenVPN
Compile o openvpn:
root # echo 'net-vpn/openvpn down-root examples iproute2 lzo pam pkcs11 plugins ssl -inotify -libressl -lz4 -mbedtls -selinux -static -systemd -test' >> /etc/portage/package.use root # emerge net-vpn/openvpn
Configuração
Crie o arquivo de configuração do cliente:
root # vi /etc/openvpn/openvpn.conf
/etc/openvpn/openvpn.conf # specify client-side
client
# tun/tap device
dev tun0
# protocol, according to server
proto udp
# server address
remote area31.net.br 1194
# connection
comp-lzo
resolv-retry 30
nobind
# persistent device and keys
persist-key
persist-tun
# keys settings
ca keys/ca.crt
cert keys/client1.crt
key keys/client1.key
# pull dns settings from the server
script-security 2
# Scripts
up /etc/openvpn/up.sh
down /etc/openvpn/down.sh
# logging
log /var/log/openvpn.log
verb 4
# 2FA Google Auth
# password generated using script /usr/sbin/connect-vpn-2fa.sh
ns-cert-type server
auth-user-pass /etc/openvpn/pass.txt
Servidor Dante Proxy (sock5)
Compile o ebuild net-proxy/dante:
root # emerge net-proxy/dante
Configure o arquivo /etc/socks/sockd.conf conforme o exemplo abaixo, alterando a rede do TUN do OpenVPN e em xxx.xxx.xxx.xxx colocando o IP de saída pra internet do seu servidor:
/etc/socks/sockd.conf logoutput: syslog
internal: 172.40.0.1 port = 1080
external: xxx.xxx.xxx.xxx
socksmethod: none
clientmethod: none
user.privileged: sockd
user.notprivileged: sockd
client pass {
from: 172.40.0.0/24 to: 0.0.0.0/0
log: error # connect disconnect
}
socks pass {
from: 0.0.0.0/0 to: 0.0.0.0/0
command: bind connect udpassociate
log: error # connect disconnect iooperation
}
socks pass {
from: 0.0.0.0/0 to: 0.0.0.0/0
command: bindreply udpreply
log: error # connect disconnect iooperation
}
Execução
Servidor OpenVPN
Adicione o servidor openvpn ao boot e inicie o daemon:
root # rc-update add openvpn ; /etc/init.d/openvpn start
Crie um usuário de VPN. Ex:
root # /usr/sbin/gen-mfa.sh teste
Será solicitada a digitação da senha. Por favor, utilize mais de 12 caracteres.
Abra a URL e escaneie o QR code no aplicativo Authy (recomendado). Também é possível utilizar o aplicativo nativo do google.
Ex:
INFO: Generating MFA Token Warning: pasting the following URL into your browser exposes the OTP secret to Google: https://www.google.com/chart?chs=200x200&chld=M|0&cht=qr&chl=otpauth://totp/OpenVPN%2520Server%3Fsecret%BRCB26KMG5R7TKQQXUBVW7D6A3%26issuer%3Dteste Failed to use libqrencode to show QR code visually for scanning. Consider typing the OTP secret into your app manually. Your new secret key is: BRCB26KMG5R7TKQQXUBVW7D6A3 Your verification code is 125654 Your emergency scratch codes are: 39144468 67723481 53844065 41433310 22803440 By default, a new token is generated every 30 seconds by the mobile app. In order to compensate for possible time-skew between the client and the server, we allow an extra token before and after the current time. This allows for a time skew of up to 30 seconds between authentication server and client. If you experience problems with poor time synchronization, you can increase the window from its default size of 3 permitted codes (one previous code, the current code, the next code) to 17 permitted codes (the 8 previous codes, the current code, and the 8 next codes). This will permit for a time skew of up to 4 minutes between client and server. Do you want to do so? (y/n) y
Cliente OpenVPN
crie um script para autenticação da openvpn. Será criado randomicamente o arquivo contendo usuário e senha no formato adequado, digitando a senha criada via /usr/bin/passwd no servidor + MFA gerada no aplicativo.
root # touch /usr/sbin/connect-vpn-2fa.sh ; chmod +x /usr/sbin/connect-vpn-2fa.sh ; vi /usr/sbin/connect-vpn-2fa.sh
/usr/sbin/connect-vpn-2fa.sh - script para conexão do cliente#!/bin/bash
echo -e "\nDigite o usuário:"
read USERNAME
echo -e "\nDigite a senha:"
unset password;
while IFS= read -r -s -n1 pass; do
if [[ -z $pass ]]; then
echo
break
else
echo -n '*'
PASSWD+=$pass
fi
done
echo -e "\nDigite o codigo MFA gerado em seu celular:"
read MFA
echo -e "${USERNAME}\n${PASSWD}${MFA}" > /etc/openvpn/pass.txt ; /etc/init.d/openvpn restart
Execute o script:
root # /usr/sbin/connect-vpn-2fa.sh
Ex:
root # /usr/sbin/connect-vpn-2fa.sh
root ##i##Digite o usuário: coffnix root ##i##Digite a senha: ***************************************************** root ##i##Digite o codigo MFA gerado em seu celular: 722359
Demonstração
Log servidor
Acompanhe no log do servidor, deverá ser algo do tipo:
root # cat /var/log/openvpn.log
Sat Jun 30 20:49:56 2018 us=485682 Current Parameter Settings: Sat Jun 30 20:49:56 2018 us=485808 config = '/etc/openvpn/openvpn.conf' Sat Jun 30 20:49:56 2018 us=485832 mode = 1 Sat Jun 30 20:49:56 2018 us=485850 persist_config = DISABLED Sat Jun 30 20:49:56 2018 us=485883 persist_mode = 1 Sat Jun 30 20:49:56 2018 us=485904 show_ciphers = DISABLED Sat Jun 30 20:49:56 2018 us=485922 show_digests = DISABLED Sat Jun 30 20:49:56 2018 us=485939 show_engines = DISABLED Sat Jun 30 20:49:56 2018 us=485957 genkey = DISABLED Sat Jun 30 20:49:56 2018 us=485975 key_pass_file = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=485992 show_tls_ciphers = DISABLED Sat Jun 30 20:49:56 2018 us=486011 connect_retry_max = 0 Sat Jun 30 20:49:56 2018 us=486028 Connection profiles [0]: Sat Jun 30 20:49:56 2018 us=486047 proto = udp Sat Jun 30 20:49:56 2018 us=486065 local = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=486083 local_port = '1194' Sat Jun 30 20:49:56 2018 us=486101 remote = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=486118 remote_port = '1194' Sat Jun 30 20:49:56 2018 us=486136 remote_float = DISABLED Sat Jun 30 20:49:56 2018 us=486154 bind_defined = DISABLED Sat Jun 30 20:49:56 2018 us=486171 bind_local = ENABLED Sat Jun 30 20:49:56 2018 us=486189 bind_ipv6_only = DISABLED Sat Jun 30 20:49:56 2018 us=486207 connect_retry_seconds = 5 Sat Jun 30 20:49:56 2018 us=486225 connect_timeout = 120 Sat Jun 30 20:49:56 2018 us=486243 socks_proxy_server = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=486260 socks_proxy_port = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=486278 tun_mtu = 1500 Sat Jun 30 20:49:56 2018 us=486296 tun_mtu_defined = ENABLED Sat Jun 30 20:49:56 2018 us=486314 link_mtu = 1500 Sat Jun 30 20:49:56 2018 us=486331 link_mtu_defined = DISABLED Sat Jun 30 20:49:56 2018 us=486349 tun_mtu_extra = 0 Sat Jun 30 20:49:56 2018 us=486367 tun_mtu_extra_defined = DISABLED Sat Jun 30 20:49:56 2018 us=486384 mtu_discover_type = -1 Sat Jun 30 20:49:56 2018 us=486402 fragment = 0 Sat Jun 30 20:49:56 2018 us=486420 mssfix = 1450 Sat Jun 30 20:49:56 2018 us=486437 explicit_exit_notification = 0 Sat Jun 30 20:49:56 2018 us=486455 Connection profiles END Sat Jun 30 20:49:56 2018 us=486473 remote_random = DISABLED Sat Jun 30 20:49:56 2018 us=486491 ipchange = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=486508 dev = 'tun0' Sat Jun 30 20:49:56 2018 us=486526 dev_type = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=486543 dev_node = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=486561 lladdr = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=486578 topology = 1 Sat Jun 30 20:49:56 2018 us=486596 ifconfig_local = '10.100.0.1' Sat Jun 30 20:49:56 2018 us=486614 ifconfig_remote_netmask = '10.100.0.2' Sat Jun 30 20:49:56 2018 us=486632 ifconfig_noexec = DISABLED Sat Jun 30 20:49:56 2018 us=486649 ifconfig_nowarn = DISABLED Sat Jun 30 20:49:56 2018 us=486667 ifconfig_ipv6_local = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=486685 ifconfig_ipv6_netbits = 0 Sat Jun 30 20:49:56 2018 us=486702 ifconfig_ipv6_remote = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=486720 shaper = 0 Sat Jun 30 20:49:56 2018 us=486738 mtu_test = 0 Sat Jun 30 20:49:56 2018 us=486756 mlock = DISABLED Sat Jun 30 20:49:56 2018 us=486774 keepalive_ping = 10 Sat Jun 30 20:49:56 2018 us=486791 keepalive_timeout = 120 Sat Jun 30 20:49:56 2018 us=486809 inactivity_timeout = 0 Sat Jun 30 20:49:56 2018 us=486827 ping_send_timeout = 10 Sat Jun 30 20:49:56 2018 us=486844 ping_rec_timeout = 240 Sat Jun 30 20:49:56 2018 us=486862 ping_rec_timeout_action = 2 Sat Jun 30 20:49:56 2018 us=486880 ping_timer_remote = DISABLED Sat Jun 30 20:49:56 2018 us=486897 remap_sigusr1 = 0 Sat Jun 30 20:49:56 2018 us=486915 persist_tun = ENABLED Sat Jun 30 20:49:56 2018 us=486932 persist_local_ip = DISABLED Sat Jun 30 20:49:56 2018 us=486950 persist_remote_ip = DISABLED Sat Jun 30 20:49:56 2018 us=486968 persist_key = ENABLED Sat Jun 30 20:49:56 2018 us=486986 passtos = DISABLED Sat Jun 30 20:49:56 2018 us=487013 resolve_retry_seconds = 1000000000 Sat Jun 30 20:49:56 2018 us=487032 resolve_in_advance = DISABLED Sat Jun 30 20:49:56 2018 us=487050 username = 'nobody' Sat Jun 30 20:49:56 2018 us=487068 groupname = 'nobody' Sat Jun 30 20:49:56 2018 us=487086 chroot_dir = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=487104 cd_dir = '/etc/openvpn' Sat Jun 30 20:49:56 2018 us=487122 writepid = '/var/run/openvpn.pid' Sat Jun 30 20:49:56 2018 us=487139 up_script = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=487157 down_script = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=487175 down_pre = DISABLED Sat Jun 30 20:49:56 2018 us=487192 up_restart = DISABLED Sat Jun 30 20:49:56 2018 us=487210 up_delay = DISABLED Sat Jun 30 20:49:56 2018 us=487227 daemon = ENABLED Sat Jun 30 20:49:56 2018 us=487244 inetd = 0 Sat Jun 30 20:49:56 2018 us=487262 log = ENABLED Sat Jun 30 20:49:56 2018 us=487279 suppress_timestamps = DISABLED Sat Jun 30 20:49:56 2018 us=487297 machine_readable_output = DISABLED Sat Jun 30 20:49:56 2018 us=487314 nice = 0 Sat Jun 30 20:49:56 2018 us=487332 verbosity = 4 Sat Jun 30 20:49:56 2018 us=487349 mute = 0 Sat Jun 30 20:49:56 2018 us=487366 gremlin = 0 Sat Jun 30 20:49:56 2018 us=487384 status_file = 'openvpn-status.log' Sat Jun 30 20:49:56 2018 us=487402 status_file_version = 1 Sat Jun 30 20:49:56 2018 us=487420 status_file_update_freq = 60 Sat Jun 30 20:49:56 2018 us=487437 occ = ENABLED Sat Jun 30 20:49:56 2018 us=487456 rcvbuf = 0 Sat Jun 30 20:49:56 2018 us=487473 sndbuf = 0 Sat Jun 30 20:49:56 2018 us=487491 mark = 0 Sat Jun 30 20:49:56 2018 us=487508 sockflags = 0 Sat Jun 30 20:49:56 2018 us=487526 fast_io = DISABLED Sat Jun 30 20:49:56 2018 us=487543 comp.alg = 2 Sat Jun 30 20:49:56 2018 us=487561 comp.flags = 1 Sat Jun 30 20:49:56 2018 us=487579 route_script = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=487596 route_default_gateway = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=487614 route_default_metric = 0 Sat Jun 30 20:49:56 2018 us=487632 route_noexec = DISABLED Sat Jun 30 20:49:56 2018 us=487650 route_delay = 0 Sat Jun 30 20:49:56 2018 us=487668 route_delay_window = 30 Sat Jun 30 20:49:56 2018 us=487686 route_delay_defined = DISABLED Sat Jun 30 20:49:56 2018 us=487703 route_nopull = DISABLED Sat Jun 30 20:49:56 2018 us=487721 route_gateway_via_dhcp = DISABLED Sat Jun 30 20:49:56 2018 us=487739 allow_pull_fqdn = DISABLED Sat Jun 30 20:49:56 2018 us=487762 route 10.100.0.0/255.255.255.0/default (not set)/default (not set) Sat Jun 30 20:49:56 2018 us=487781 management_addr = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=487800 management_port = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=487817 management_user_pass = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=487835 management_log_history_cache = 250 Sat Jun 30 20:49:56 2018 us=487853 management_echo_buffer_size = 100 Sat Jun 30 20:49:56 2018 us=487871 management_write_peer_info_file = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=487889 management_client_user = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=487907 management_client_group = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=487925 management_flags = 0 Sat Jun 30 20:49:56 2018 us=487951 plugin[0] /usr/lib64/openvpn/plugins/openvpn-plugin-auth-pam.so '[/usr/lib64/openvpn/plugins/openvpn-plugin-auth-pam.so] [openvpn]' Sat Jun 30 20:49:56 2018 us=487975 shared_secret_file = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=487993 key_direction = not set Sat Jun 30 20:49:56 2018 us=488011 ciphername = 'BF-CBC' Sat Jun 30 20:49:56 2018 us=488029 ncp_enabled = ENABLED Sat Jun 30 20:49:56 2018 us=488046 ncp_ciphers = 'AES-256-GCM:AES-128-GCM' Sat Jun 30 20:49:56 2018 us=488064 authname = 'SHA1' Sat Jun 30 20:49:56 2018 us=488082 prng_hash = 'SHA1' Sat Jun 30 20:49:56 2018 us=488100 prng_nonce_secret_len = 16 Sat Jun 30 20:49:56 2018 us=488117 keysize = 0 Sat Jun 30 20:49:56 2018 us=488135 engine = DISABLED Sat Jun 30 20:49:56 2018 us=488152 replay = ENABLED Sat Jun 30 20:49:56 2018 us=488170 mute_replay_warnings = DISABLED Sat Jun 30 20:49:56 2018 us=488188 replay_window = 64 Sat Jun 30 20:49:56 2018 us=488205 replay_time = 15 Sat Jun 30 20:49:56 2018 us=488223 packet_id_file = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=488240 use_iv = ENABLED Sat Jun 30 20:49:56 2018 us=488258 test_crypto = DISABLED Sat Jun 30 20:49:56 2018 us=488275 tls_server = ENABLED Sat Jun 30 20:49:56 2018 us=488293 tls_client = DISABLED Sat Jun 30 20:49:56 2018 us=488311 key_method = 2 Sat Jun 30 20:49:56 2018 us=488329 ca_file = '/etc/openvpn/keys/pki/ca.crt' Sat Jun 30 20:49:56 2018 us=488346 ca_path = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=488364 dh_file = '/etc/openvpn/keys/pki/dh.pem' Sat Jun 30 20:49:56 2018 us=488382 cert_file = '/etc/openvpn/keys/pki/issued/FuntooHost.crt' Sat Jun 30 20:49:56 2018 us=488401 extra_certs_file = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=488419 priv_key_file = '/etc/openvpn/keys/pki/private/FuntooHost.key' Sat Jun 30 20:49:56 2018 us=488438 pkcs12_file = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=488455 cipher_list = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=488473 tls_cert_profile = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=488491 tls_verify = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=488508 tls_export_cert = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=488526 verify_x509_type = 0 Sat Jun 30 20:49:56 2018 us=488544 verify_x509_name = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=488562 crl_file = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=488580 ns_cert_type = 0 Sat Jun 30 20:49:56 2018 us=488597 remote_cert_ku[i] = 0 Sat Jun 30 20:49:56 2018 us=488615 remote_cert_ku[i] = 0 Sat Jun 30 20:49:56 2018 us=488633 remote_cert_ku[i] = 0 Sat Jun 30 20:49:56 2018 us=488650 remote_cert_ku[i] = 0 Sat Jun 30 20:49:56 2018 us=488668 remote_cert_ku[i] = 0 Sat Jun 30 20:49:56 2018 us=488685 remote_cert_ku[i] = 0 Sat Jun 30 20:49:56 2018 us=488703 remote_cert_ku[i] = 0 Sat Jun 30 20:49:56 2018 us=488721 remote_cert_ku[i] = 0 Sat Jun 30 20:49:56 2018 us=488739 remote_cert_ku[i] = 0 Sat Jun 30 20:49:56 2018 us=488756 remote_cert_ku[i] = 0 Sat Jun 30 20:49:56 2018 us=488774 remote_cert_ku[i] = 0 Sat Jun 30 20:49:56 2018 us=488791 remote_cert_ku[i] = 0 Sat Jun 30 20:49:56 2018 us=488809 remote_cert_ku[i] = 0 Sat Jun 30 20:49:56 2018 us=488826 remote_cert_ku[i] = 0 Sat Jun 30 20:49:56 2018 us=488843 remote_cert_ku[i] = 0 Sat Jun 30 20:49:56 2018 us=488861 remote_cert_ku[i] = 0 Sat Jun 30 20:49:56 2018 us=488878 remote_cert_eku = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=488896 ssl_flags = 0 Sat Jun 30 20:49:56 2018 us=488914 tls_timeout = 2 Sat Jun 30 20:49:56 2018 us=488931 renegotiate_bytes = -1 Sat Jun 30 20:49:56 2018 us=488948 renegotiate_packets = 0 Sat Jun 30 20:49:56 2018 us=488966 renegotiate_seconds = 3600 Sat Jun 30 20:49:56 2018 us=488984 handshake_window = 60 Sat Jun 30 20:49:56 2018 us=489002 transition_window = 3600 Sat Jun 30 20:49:56 2018 us=489020 single_session = DISABLED Sat Jun 30 20:49:56 2018 us=489038 push_peer_info = DISABLED Sat Jun 30 20:49:56 2018 us=489056 tls_exit = DISABLED Sat Jun 30 20:49:56 2018 us=489074 tls_auth_file = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=489091 tls_crypt_file = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=489110 pkcs11_protected_authentication = DISABLED Sat Jun 30 20:49:56 2018 us=489128 pkcs11_protected_authentication = DISABLED Sat Jun 30 20:49:56 2018 us=489146 pkcs11_protected_authentication = DISABLED Sat Jun 30 20:49:56 2018 us=489164 pkcs11_protected_authentication = DISABLED Sat Jun 30 20:49:56 2018 us=489182 pkcs11_protected_authentication = DISABLED Sat Jun 30 20:49:56 2018 us=489200 pkcs11_protected_authentication = DISABLED Sat Jun 30 20:49:56 2018 us=489218 pkcs11_protected_authentication = DISABLED Sat Jun 30 20:49:56 2018 us=489236 pkcs11_protected_authentication = DISABLED Sat Jun 30 20:49:56 2018 us=489254 pkcs11_protected_authentication = DISABLED Sat Jun 30 20:49:56 2018 us=489272 pkcs11_protected_authentication = DISABLED Sat Jun 30 20:49:56 2018 us=489290 pkcs11_protected_authentication = DISABLED Sat Jun 30 20:49:56 2018 us=489308 pkcs11_protected_authentication = DISABLED Sat Jun 30 20:49:56 2018 us=489326 pkcs11_protected_authentication = DISABLED Sat Jun 30 20:49:56 2018 us=489344 pkcs11_protected_authentication = DISABLED Sat Jun 30 20:49:56 2018 us=489362 pkcs11_protected_authentication = DISABLED Sat Jun 30 20:49:56 2018 us=489380 pkcs11_protected_authentication = DISABLED Sat Jun 30 20:49:56 2018 us=489399 pkcs11_private_mode = 00000000 Sat Jun 30 20:49:56 2018 us=489418 pkcs11_private_mode = 00000000 Sat Jun 30 20:49:56 2018 us=489436 pkcs11_private_mode = 00000000 Sat Jun 30 20:49:56 2018 us=489454 pkcs11_private_mode = 00000000 Sat Jun 30 20:49:56 2018 us=489471 pkcs11_private_mode = 00000000 Sat Jun 30 20:49:56 2018 us=489490 pkcs11_private_mode = 00000000 Sat Jun 30 20:49:56 2018 us=489508 pkcs11_private_mode = 00000000 Sat Jun 30 20:49:56 2018 us=489526 pkcs11_private_mode = 00000000 Sat Jun 30 20:49:56 2018 us=489544 pkcs11_private_mode = 00000000 Sat Jun 30 20:49:56 2018 us=489562 pkcs11_private_mode = 00000000 Sat Jun 30 20:49:56 2018 us=489580 pkcs11_private_mode = 00000000 Sat Jun 30 20:49:56 2018 us=489598 pkcs11_private_mode = 00000000 Sat Jun 30 20:49:56 2018 us=489616 pkcs11_private_mode = 00000000 Sat Jun 30 20:49:56 2018 us=489633 pkcs11_private_mode = 00000000 Sat Jun 30 20:49:56 2018 us=489651 pkcs11_private_mode = 00000000 Sat Jun 30 20:49:56 2018 us=489670 pkcs11_private_mode = 00000000 Sat Jun 30 20:49:56 2018 us=489688 pkcs11_cert_private = DISABLED Sat Jun 30 20:49:56 2018 us=489706 pkcs11_cert_private = DISABLED Sat Jun 30 20:49:56 2018 us=489724 pkcs11_cert_private = DISABLED Sat Jun 30 20:49:56 2018 us=489743 pkcs11_cert_private = DISABLED Sat Jun 30 20:49:56 2018 us=489761 pkcs11_cert_private = DISABLED Sat Jun 30 20:49:56 2018 us=489779 pkcs11_cert_private = DISABLED Sat Jun 30 20:49:56 2018 us=489797 pkcs11_cert_private = DISABLED Sat Jun 30 20:49:56 2018 us=489815 pkcs11_cert_private = DISABLED Sat Jun 30 20:49:56 2018 us=489833 pkcs11_cert_private = DISABLED Sat Jun 30 20:49:56 2018 us=489851 pkcs11_cert_private = DISABLED Sat Jun 30 20:49:56 2018 us=489877 pkcs11_cert_private = DISABLED Sat Jun 30 20:49:56 2018 us=489900 pkcs11_cert_private = DISABLED Sat Jun 30 20:49:56 2018 us=489918 pkcs11_cert_private = DISABLED Sat Jun 30 20:49:56 2018 us=489936 pkcs11_cert_private = DISABLED Sat Jun 30 20:49:56 2018 us=489954 pkcs11_cert_private = DISABLED Sat Jun 30 20:49:56 2018 us=489971 pkcs11_cert_private = DISABLED Sat Jun 30 20:49:56 2018 us=489990 pkcs11_pin_cache_period = -1 Sat Jun 30 20:49:56 2018 us=490007 pkcs11_id = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=490025 pkcs11_id_management = DISABLED Sat Jun 30 20:49:56 2018 us=490044 server_network = 10.100.0.0 Sat Jun 30 20:49:56 2018 us=490062 server_netmask = 255.255.255.0 Sat Jun 30 20:49:56 2018 us=490085 server_network_ipv6 = :: Sat Jun 30 20:49:56 2018 us=490105 server_netbits_ipv6 = 0 Sat Jun 30 20:49:56 2018 us=490124 server_bridge_ip = 0.0.0.0 Sat Jun 30 20:49:56 2018 us=490142 server_bridge_netmask = 0.0.0.0 Sat Jun 30 20:49:56 2018 us=490161 server_bridge_pool_start = 0.0.0.0 Sat Jun 30 20:49:56 2018 us=490179 server_bridge_pool_end = 0.0.0.0 Sat Jun 30 20:49:56 2018 us=490197 push_entry = 'route 10.100.0.1' Sat Jun 30 20:49:56 2018 us=490215 push_entry = 'topology net30' Sat Jun 30 20:49:56 2018 us=490233 push_entry = 'ping 10' Sat Jun 30 20:49:56 2018 us=490250 push_entry = 'ping-restart 120' Sat Jun 30 20:49:56 2018 us=490268 ifconfig_pool_defined = ENABLED Sat Jun 30 20:49:56 2018 us=490286 ifconfig_pool_start = 10.100.0.4 Sat Jun 30 20:49:56 2018 us=490304 ifconfig_pool_end = 10.100.0.251 Sat Jun 30 20:49:56 2018 us=490323 ifconfig_pool_netmask = 0.0.0.0 Sat Jun 30 20:49:56 2018 us=490340 ifconfig_pool_persist_filename = 'ipp.txt' Sat Jun 30 20:49:56 2018 us=490358 ifconfig_pool_persist_refresh_freq = 600 Sat Jun 30 20:49:56 2018 us=490376 ifconfig_ipv6_pool_defined = DISABLED Sat Jun 30 20:49:56 2018 us=490396 ifconfig_ipv6_pool_base = :: Sat Jun 30 20:49:56 2018 us=490415 ifconfig_ipv6_pool_netbits = 0 Sat Jun 30 20:49:56 2018 us=490433 n_bcast_buf = 256 Sat Jun 30 20:49:56 2018 us=490451 tcp_queue_limit = 64 Sat Jun 30 20:49:56 2018 us=490468 real_hash_size = 256 Sat Jun 30 20:49:56 2018 us=490486 virtual_hash_size = 256 Sat Jun 30 20:49:56 2018 us=490503 client_connect_script = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=490522 learn_address_script = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=490540 client_disconnect_script = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=490557 client_config_dir = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=490575 ccd_exclusive = DISABLED Sat Jun 30 20:49:56 2018 us=490593 tmp_dir = '/tmp' Sat Jun 30 20:49:56 2018 us=490610 push_ifconfig_defined = DISABLED Sat Jun 30 20:49:56 2018 us=490629 push_ifconfig_local = 0.0.0.0 Sat Jun 30 20:49:56 2018 us=490647 push_ifconfig_remote_netmask = 0.0.0.0 Sat Jun 30 20:49:56 2018 us=490665 push_ifconfig_ipv6_defined = DISABLED Sat Jun 30 20:49:56 2018 us=490684 push_ifconfig_ipv6_local = ::/0 Sat Jun 30 20:49:56 2018 us=490702 push_ifconfig_ipv6_remote = :: Sat Jun 30 20:49:56 2018 us=490720 enable_c2c = DISABLED Sat Jun 30 20:49:56 2018 us=490738 duplicate_cn = DISABLED Sat Jun 30 20:49:56 2018 us=490755 cf_max = 0 Sat Jun 30 20:49:56 2018 us=490773 cf_per = 0 Sat Jun 30 20:49:56 2018 us=490791 max_clients = 1024 Sat Jun 30 20:49:56 2018 us=490808 max_routes_per_client = 256 Sat Jun 30 20:49:56 2018 us=490826 auth_user_pass_verify_script = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=490843 auth_user_pass_verify_script_via_file = DISABLED Sat Jun 30 20:49:56 2018 us=490861 auth_token_generate = DISABLED Sat Jun 30 20:49:56 2018 us=490879 auth_token_lifetime = 0 Sat Jun 30 20:49:56 2018 us=490897 port_share_host = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=490915 port_share_port = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=490933 client = DISABLED Sat Jun 30 20:49:56 2018 us=490950 pull = DISABLED Sat Jun 30 20:49:56 2018 us=490968 auth_user_pass_file = '[UNDEF]' Sat Jun 30 20:49:56 2018 us=490988 OpenVPN 2.4.6 x86_64-pc-linux-gnu [SSL (OpenSSL)] [LZO] [EPOLL] [PKCS11] [MH/PKTINFO] [AEAD] built on May 29 2018 Sat Jun 30 20:49:56 2018 us=491016 library versions: OpenSSL 1.0.2o 27 Mar 2018, LZO 2.10 AUTH-PAM: BACKGROUND: INIT service='openvpn' Sat Jun 30 20:49:56 2018 us=492942 PLUGIN_INIT: POST /usr/lib64/openvpn/plugins/openvpn-plugin-auth-pam.so '[/usr/lib64/openvpn/plugins/openvpn-plugin-auth-pam.so] [openvpn]' intercepted=PLUGIN_AUTH_USER_PASS_VERIFY Sat Jun 30 20:49:56 2018 us=493447 Diffie-Hellman initialized with 2048 bit key Sat Jun 30 20:49:56 2018 us=494024 TLS-Auth MTU parms [ L:1622 D:1212 EF:38 EB:0 ET:0 EL:3 ] Sat Jun 30 20:49:56 2018 us=494333 ROUTE_GATEWAY 172.97.103.1/255.255.255.0 IFACE=eth0 HWADDR=00:16:3e:35:4c:3c Sat Jun 30 20:49:56 2018 us=494904 TUN/TAP device tun0 opened Sat Jun 30 20:49:56 2018 us=494953 Note: Cannot set tx queue length on tun0: Operation not permitted (errno=1) Sat Jun 30 20:49:56 2018 us=494986 do_ifconfig, tt->did_ifconfig_ipv6_setup=0 Sat Jun 30 20:49:56 2018 us=495014 /sbin/ip link set dev tun0 up mtu 1500 Sat Jun 30 20:49:56 2018 us=497424 /sbin/ip addr add dev tun0 local 10.100.0.1 peer 10.100.0.2 Sat Jun 30 20:49:56 2018 us=500205 /sbin/ip route add 10.100.0.0/24 via 10.100.0.2 Sat Jun 30 20:49:56 2018 us=501714 Data Channel MTU parms [ L:1622 D:1450 EF:122 EB:406 ET:0 EL:3 AF:3/1 ] Sat Jun 30 20:49:56 2018 us=502617 Could not determine IPv4/IPv6 protocol. Using AF_INET Sat Jun 30 20:49:56 2018 us=502670 Socket Buffers: R=[33554432->33554432] S=[33554432->33554432] Sat Jun 30 20:49:56 2018 us=502711 UDPv4 link local (bound): [AF_INET][undef]:1194 Sat Jun 30 20:49:56 2018 us=502733 UDPv4 link remote: [AF_UNSPEC] Sat Jun 30 20:49:56 2018 us=502761 GID set to nobody Sat Jun 30 20:49:56 2018 us=502796 UID set to nobody Sat Jun 30 20:49:56 2018 us=502832 MULTI: multi_init called, r=256 v=256 Sat Jun 30 20:49:56 2018 us=502892 IFCONFIG POOL: base=10.100.0.4 size=62, ipv6=0 Sat Jun 30 20:49:56 2018 us=502941 ifconfig_pool_read(), in='client1,10.100.0.4', TODO: IPv6 Sat Jun 30 20:49:56 2018 us=502966 succeeded -> ifconfig_pool_set() Sat Jun 30 20:49:56 2018 us=502989 IFCONFIG POOL LIST Sat Jun 30 20:49:56 2018 us=503009 client1,10.100.0.4 Sat Jun 30 20:49:56 2018 us=503051 Initialization Sequence Completed Sat Jun 30 20:50:22 2018 us=54652 MULTI: multi_create_instance called Sat Jun 30 20:50:22 2018 us=54856 187.104.48.10:59146 Re-using SSL/TLS context Sat Jun 30 20:50:22 2018 us=54904 187.104.48.10:59146 LZO compression initializing Sat Jun 30 20:50:22 2018 us=55088 187.104.48.10:59146 Control Channel MTU parms [ L:1622 D:1212 EF:38 EB:0 ET:0 EL:3 ] Sat Jun 30 20:50:22 2018 us=55123 187.104.48.10:59146 Data Channel MTU parms [ L:1622 D:1450 EF:122 EB:406 ET:0 EL:3 AF:3/1 ] Sat Jun 30 20:50:22 2018 us=55176 187.104.48.10:59146 Local Options String (VER=V4): 'V4,dev-type tun,link-mtu 1542,tun-mtu 1500,proto UDPv4,comp-lzo,cipher BF-CBC,auth SHA1,keysize 128,key-method 2,tls-server' Sat Jun 30 20:50:22 2018 us=55202 187.104.48.10:59146 Expected Remote Options String (VER=V4): 'V4,dev-type tun,link-mtu 1542,tun-mtu 1500,proto UDPv4,comp-lzo,cipher BF-CBC,auth SHA1,keysize 128,key-method 2,tls-client' Sat Jun 30 20:50:22 2018 us=55265 187.104.48.10:59146 TLS: Initial packet from [AF_INET]187.104.48.10:59146, sid=649b0f94 1844f9aa Sat Jun 30 20:50:22 2018 us=645519 187.104.48.10:59146 VERIFY OK: depth=1, CN=FuntooHost Sat Jun 30 20:50:22 2018 us=645819 187.104.48.10:59146 VERIFY OK: depth=0, CN=client1 Sat Jun 30 20:50:22 2018 us=935014 187.104.48.10:59146 peer info: IV_VER=2.4.6 Sat Jun 30 20:50:22 2018 us=935095 187.104.48.10:59146 peer info: IV_PLAT=linux Sat Jun 30 20:50:22 2018 us=935118 187.104.48.10:59146 peer info: IV_PROTO=2 Sat Jun 30 20:50:22 2018 us=935137 187.104.48.10:59146 peer info: IV_NCP=2 Sat Jun 30 20:50:22 2018 us=935156 187.104.48.10:59146 peer info: IV_LZO=1 Sat Jun 30 20:50:22 2018 us=935176 187.104.48.10:59146 peer info: IV_COMP_STUB=1 Sat Jun 30 20:50:22 2018 us=935195 187.104.48.10:59146 peer info: IV_COMP_STUBv2=1 Sat Jun 30 20:50:22 2018 us=935214 187.104.48.10:59146 peer info: IV_TCPNL=1 AUTH-PAM: BACKGROUND: received command code: 0 AUTH-PAM: BACKGROUND: USER: coffnix AUTH-PAM: BACKGROUND: my_conv[0] query='Password & verification code: ' style=1 Sat Jun 30 20:50:22 2018 us=952869 187.104.48.10:59146 PLUGIN_CALL: POST /usr/lib64/openvpn/plugins/openvpn-plugin-auth-pam.so/PLUGIN_AUTH_USER_PASS_VERIFY status=0 Sat Jun 30 20:50:22 2018 us=953049 187.104.48.10:59146 TLS: Username/Password authentication succeeded for username 'coffnix' Sat Jun 30 20:50:23 2018 us=241062 187.104.48.10:59146 Control Channel: TLSv1.2, cipher TLSv1/SSLv3 ECDHE-RSA-AES256-GCM-SHA384, 2048 bit RSA Sat Jun 30 20:50:23 2018 us=241203 187.104.48.10:59146 [client1] Peer Connection Initiated with [AF_INET]187.104.48.10:59146 Sat Jun 30 20:50:23 2018 us=241263 client1/187.104.48.10:59146 MULTI_sva: pool returned IPv4=10.100.0.6, IPv6=(Not enabled) Sat Jun 30 20:50:23 2018 us=241322 client1/187.104.48.10:59146 MULTI: Learn: 10.100.0.6 -> client1/187.104.48.10:59146 Sat Jun 30 20:50:23 2018 us=241344 client1/187.104.48.10:59146 MULTI: primary virtual IP for client1/187.104.48.10:59146: 10.100.0.6 Sat Jun 30 20:50:24 2018 us=458952 client1/187.104.48.10:59146 PUSH: Received control message: 'PUSH_REQUEST' Sat Jun 30 20:50:24 2018 us=459102 client1/187.104.48.10:59146 SENT CONTROL [client1]: 'PUSH_REPLY,route 10.100.0.1,topology net30,ping 10,ping-restart 120,ifconfig 10.100.0.6 10.100.0.5,peer-id 0,cipher AES-256-GCM' (status=1) Sat Jun 30 20:50:24 2018 us=459130 client1/187.104.48.10:59146 Data Channel: using negotiated cipher 'AES-256-GCM' Sat Jun 30 20:50:24 2018 us=459164 client1/187.104.48.10:59146 Data Channel MTU parms [ L:1550 D:1450 EF:50 EB:406 ET:0 EL:3 AF:3/1 ] Sat Jun 30 20:50:24 2018 us=459306 client1/187.104.48.10:59146 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key Sat Jun 30 20:50:24 2018 us=459335 client1/187.104.48.10:59146 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key Sat Jun 30 20:50:29 2018 us=762034 client1/187.104.48.10:59146 PID_ERR replay-window backtrack occurred [1] [SSL-0] [0_00123] 0:7 0:6 t=1530402629[0] r=[-3,64,15,1,1] sl=[57,7,64,528]
Log Cliente
Acompanhe no log do cliente, deverá ser algo do tipo:
root # cat /var/log/openvpn.log
Sat Jun 30 20:50:21 2018 Multiple --up scripts defined. The previously configured script is overridden. Sat Jun 30 20:50:21 2018 Multiple --down scripts defined. The previously configured script is overridden. Sat Jun 30 20:50:21 2018 us=566336 WARNING: file '/etc/openvpn/pass.txt' is group or others accessible Sat Jun 30 20:50:21 2018 us=566354 Current Parameter Settings: Sat Jun 30 20:50:21 2018 us=566361 config = '/etc/openvpn/openvpn.conf' Sat Jun 30 20:50:21 2018 us=566367 mode = 0 Sat Jun 30 20:50:21 2018 us=566373 persist_config = DISABLED Sat Jun 30 20:50:21 2018 us=566379 persist_mode = 1 Sat Jun 30 20:50:21 2018 us=566385 show_ciphers = DISABLED Sat Jun 30 20:50:21 2018 us=566391 show_digests = DISABLED Sat Jun 30 20:50:21 2018 us=566396 show_engines = DISABLED Sat Jun 30 20:50:21 2018 us=566402 genkey = DISABLED Sat Jun 30 20:50:21 2018 us=566408 key_pass_file = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=566414 show_tls_ciphers = DISABLED Sat Jun 30 20:50:21 2018 us=566419 connect_retry_max = 0 Sat Jun 30 20:50:21 2018 us=566425 Connection profiles [0]: Sat Jun 30 20:50:21 2018 us=566431 proto = udp Sat Jun 30 20:50:21 2018 us=566437 local = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=566443 local_port = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=566451 remote = 'area31.net.br' Sat Jun 30 20:50:21 2018 us=566457 remote_port = '1194' Sat Jun 30 20:50:21 2018 us=566463 remote_float = DISABLED Sat Jun 30 20:50:21 2018 us=566469 bind_defined = DISABLED Sat Jun 30 20:50:21 2018 us=566474 bind_local = DISABLED Sat Jun 30 20:50:21 2018 us=566480 bind_ipv6_only = DISABLED Sat Jun 30 20:50:21 2018 us=566486 connect_retry_seconds = 5 Sat Jun 30 20:50:21 2018 us=566492 connect_timeout = 120 Sat Jun 30 20:50:21 2018 us=566497 socks_proxy_server = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=566503 socks_proxy_port = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=566509 tun_mtu = 1500 Sat Jun 30 20:50:21 2018 us=566515 tun_mtu_defined = ENABLED Sat Jun 30 20:50:21 2018 us=566521 link_mtu = 1500 Sat Jun 30 20:50:21 2018 us=566526 link_mtu_defined = DISABLED Sat Jun 30 20:50:21 2018 us=566532 tun_mtu_extra = 0 Sat Jun 30 20:50:21 2018 us=566538 tun_mtu_extra_defined = DISABLED Sat Jun 30 20:50:21 2018 us=566544 mtu_discover_type = -1 Sat Jun 30 20:50:21 2018 us=566550 fragment = 0 Sat Jun 30 20:50:21 2018 us=566555 mssfix = 1450 Sat Jun 30 20:50:21 2018 us=566561 explicit_exit_notification = 0 Sat Jun 30 20:50:21 2018 us=566567 Connection profiles END Sat Jun 30 20:50:21 2018 us=566573 remote_random = DISABLED Sat Jun 30 20:50:21 2018 us=566578 ipchange = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=566584 dev = 'tun0' Sat Jun 30 20:50:21 2018 us=566590 dev_type = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=566596 dev_node = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=566602 lladdr = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=566607 topology = 1 Sat Jun 30 20:50:21 2018 us=566613 ifconfig_local = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=566619 ifconfig_remote_netmask = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=566625 ifconfig_noexec = DISABLED Sat Jun 30 20:50:21 2018 us=566630 ifconfig_nowarn = DISABLED Sat Jun 30 20:50:21 2018 us=566636 ifconfig_ipv6_local = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=566642 ifconfig_ipv6_netbits = 0 Sat Jun 30 20:50:21 2018 us=566647 ifconfig_ipv6_remote = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=566653 shaper = 0 Sat Jun 30 20:50:21 2018 us=566659 mtu_test = 0 Sat Jun 30 20:50:21 2018 us=566665 mlock = DISABLED Sat Jun 30 20:50:21 2018 us=566671 keepalive_ping = 0 Sat Jun 30 20:50:21 2018 us=566676 keepalive_timeout = 0 Sat Jun 30 20:50:21 2018 us=566682 inactivity_timeout = 0 Sat Jun 30 20:50:21 2018 us=566688 ping_send_timeout = 0 Sat Jun 30 20:50:21 2018 us=566693 ping_rec_timeout = 0 Sat Jun 30 20:50:21 2018 us=566699 ping_rec_timeout_action = 0 Sat Jun 30 20:50:21 2018 us=566705 ping_timer_remote = DISABLED Sat Jun 30 20:50:21 2018 us=566710 remap_sigusr1 = 0 Sat Jun 30 20:50:21 2018 us=566716 persist_tun = ENABLED Sat Jun 30 20:50:21 2018 us=566722 persist_local_ip = DISABLED Sat Jun 30 20:50:21 2018 us=566732 persist_remote_ip = DISABLED Sat Jun 30 20:50:21 2018 us=566738 persist_key = ENABLED Sat Jun 30 20:50:21 2018 us=566744 passtos = DISABLED Sat Jun 30 20:50:21 2018 us=566750 resolve_retry_seconds = 30 Sat Jun 30 20:50:21 2018 us=566756 resolve_in_advance = DISABLED Sat Jun 30 20:50:21 2018 us=566761 username = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=566767 groupname = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=566773 chroot_dir = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=566779 cd_dir = '/etc/openvpn' Sat Jun 30 20:50:21 2018 us=566784 writepid = '/var/run/openvpn.pid' Sat Jun 30 20:50:21 2018 us=566790 up_script = '/etc/openvpn/up.sh' Sat Jun 30 20:50:21 2018 us=566796 down_script = '/etc/openvpn/down.sh' Sat Jun 30 20:50:21 2018 us=566802 down_pre = ENABLED Sat Jun 30 20:50:21 2018 us=566807 up_restart = ENABLED Sat Jun 30 20:50:21 2018 us=566813 up_delay = ENABLED Sat Jun 30 20:50:21 2018 us=566819 daemon = ENABLED Sat Jun 30 20:50:21 2018 us=566825 inetd = 0 Sat Jun 30 20:50:21 2018 us=566830 log = ENABLED Sat Jun 30 20:50:21 2018 us=566836 suppress_timestamps = DISABLED Sat Jun 30 20:50:21 2018 us=566842 machine_readable_output = DISABLED Sat Jun 30 20:50:21 2018 us=566848 nice = 0 Sat Jun 30 20:50:21 2018 us=566853 verbosity = 4 Sat Jun 30 20:50:21 2018 us=566859 mute = 0 Sat Jun 30 20:50:21 2018 us=566865 gremlin = 0 Sat Jun 30 20:50:21 2018 us=566871 status_file = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=566876 status_file_version = 1 Sat Jun 30 20:50:21 2018 us=566882 status_file_update_freq = 60 Sat Jun 30 20:50:21 2018 us=566888 occ = ENABLED Sat Jun 30 20:50:21 2018 us=566894 rcvbuf = 0 Sat Jun 30 20:50:21 2018 us=566899 sndbuf = 0 Sat Jun 30 20:50:21 2018 us=566905 mark = 0 Sat Jun 30 20:50:21 2018 us=566911 sockflags = 0 Sat Jun 30 20:50:21 2018 us=566917 fast_io = DISABLED Sat Jun 30 20:50:21 2018 us=566923 comp.alg = 2 Sat Jun 30 20:50:21 2018 us=566928 comp.flags = 1 Sat Jun 30 20:50:21 2018 us=566934 route_script = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=566940 route_default_gateway = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=566946 route_default_metric = 0 Sat Jun 30 20:50:21 2018 us=566952 route_noexec = DISABLED Sat Jun 30 20:50:21 2018 us=566957 route_delay = 0 Sat Jun 30 20:50:21 2018 us=566963 route_delay_window = 30 Sat Jun 30 20:50:21 2018 us=566969 route_delay_defined = DISABLED Sat Jun 30 20:50:21 2018 us=566975 route_nopull = DISABLED Sat Jun 30 20:50:21 2018 us=566981 route_gateway_via_dhcp = DISABLED Sat Jun 30 20:50:21 2018 us=566987 allow_pull_fqdn = DISABLED Sat Jun 30 20:50:21 2018 us=566993 management_addr = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=566999 management_port = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=567005 management_user_pass = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=567011 management_log_history_cache = 250 Sat Jun 30 20:50:21 2018 us=567017 management_echo_buffer_size = 100 Sat Jun 30 20:50:21 2018 us=567023 management_write_peer_info_file = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=567028 management_client_user = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=567034 management_client_group = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=567040 management_flags = 0 Sat Jun 30 20:50:21 2018 us=567046 shared_secret_file = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=567052 key_direction = not set Sat Jun 30 20:50:21 2018 us=567058 ciphername = 'BF-CBC' Sat Jun 30 20:50:21 2018 us=567064 ncp_enabled = ENABLED Sat Jun 30 20:50:21 2018 us=567070 ncp_ciphers = 'AES-256-GCM:AES-128-GCM' Sat Jun 30 20:50:21 2018 us=567076 authname = 'SHA1' Sat Jun 30 20:50:21 2018 us=567081 prng_hash = 'SHA1' Sat Jun 30 20:50:21 2018 us=567087 prng_nonce_secret_len = 16 Sat Jun 30 20:50:21 2018 us=567093 keysize = 0 Sat Jun 30 20:50:21 2018 us=567099 engine = DISABLED Sat Jun 30 20:50:21 2018 us=567105 replay = ENABLED Sat Jun 30 20:50:21 2018 us=567111 mute_replay_warnings = DISABLED Sat Jun 30 20:50:21 2018 us=567117 replay_window = 64 Sat Jun 30 20:50:21 2018 us=567126 replay_time = 15 Sat Jun 30 20:50:21 2018 us=567132 packet_id_file = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=567138 use_iv = ENABLED Sat Jun 30 20:50:21 2018 us=567144 test_crypto = DISABLED Sat Jun 30 20:50:21 2018 us=567150 tls_server = DISABLED Sat Jun 30 20:50:21 2018 us=567156 tls_client = ENABLED Sat Jun 30 20:50:21 2018 us=567162 key_method = 2 Sat Jun 30 20:50:21 2018 us=567167 ca_file = 'keys/ca.crt' Sat Jun 30 20:50:21 2018 us=567180 ca_path = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=567188 dh_file = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=567194 cert_file = 'keys/client1.crt' Sat Jun 30 20:50:21 2018 us=567200 extra_certs_file = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=567206 priv_key_file = 'keys/client1.key' Sat Jun 30 20:50:21 2018 us=567212 pkcs12_file = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=567217 cipher_list = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=567223 tls_cert_profile = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=567229 tls_verify = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=567235 tls_export_cert = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=567241 verify_x509_type = 0 Sat Jun 30 20:50:21 2018 us=567246 verify_x509_name = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=567252 crl_file = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=567258 ns_cert_type = 1 Sat Jun 30 20:50:21 2018 us=567264 remote_cert_ku[i] = 0 Sat Jun 30 20:50:21 2018 us=567270 remote_cert_ku[i] = 0 Sat Jun 30 20:50:21 2018 us=567276 remote_cert_ku[i] = 0 Sat Jun 30 20:50:21 2018 us=567281 remote_cert_ku[i] = 0 Sat Jun 30 20:50:21 2018 us=567287 remote_cert_ku[i] = 0 Sat Jun 30 20:50:21 2018 us=567293 remote_cert_ku[i] = 0 Sat Jun 30 20:50:21 2018 us=567299 remote_cert_ku[i] = 0 Sat Jun 30 20:50:21 2018 us=567305 remote_cert_ku[i] = 0 Sat Jun 30 20:50:21 2018 us=567311 remote_cert_ku[i] = 0 Sat Jun 30 20:50:21 2018 us=567316 remote_cert_ku[i] = 0 Sat Jun 30 20:50:21 2018 us=567322 remote_cert_ku[i] = 0 Sat Jun 30 20:50:21 2018 us=567328 remote_cert_ku[i] = 0 Sat Jun 30 20:50:21 2018 us=567334 remote_cert_ku[i] = 0 Sat Jun 30 20:50:21 2018 us=567340 remote_cert_ku[i] = 0 Sat Jun 30 20:50:21 2018 us=567346 remote_cert_ku[i] = 0 Sat Jun 30 20:50:21 2018 us=567351 remote_cert_ku[i] = 0 Sat Jun 30 20:50:21 2018 us=567357 remote_cert_eku = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=567363 ssl_flags = 0 Sat Jun 30 20:50:21 2018 us=567369 tls_timeout = 2 Sat Jun 30 20:50:21 2018 us=567375 renegotiate_bytes = -1 Sat Jun 30 20:50:21 2018 us=567381 renegotiate_packets = 0 Sat Jun 30 20:50:21 2018 us=567387 renegotiate_seconds = 3600 Sat Jun 30 20:50:21 2018 us=567392 handshake_window = 60 Sat Jun 30 20:50:21 2018 us=567398 transition_window = 3600 Sat Jun 30 20:50:21 2018 us=567404 single_session = DISABLED Sat Jun 30 20:50:21 2018 us=567410 push_peer_info = DISABLED Sat Jun 30 20:50:21 2018 us=567416 tls_exit = DISABLED Sat Jun 30 20:50:21 2018 us=567422 tls_auth_file = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=567428 tls_crypt_file = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=567436 server_network = 0.0.0.0 Sat Jun 30 20:50:21 2018 us=567443 server_netmask = 0.0.0.0 Sat Jun 30 20:50:21 2018 us=567455 server_network_ipv6 = :: Sat Jun 30 20:50:21 2018 us=567463 server_netbits_ipv6 = 0 Sat Jun 30 20:50:21 2018 us=567470 server_bridge_ip = 0.0.0.0 Sat Jun 30 20:50:21 2018 us=567476 server_bridge_netmask = 0.0.0.0 Sat Jun 30 20:50:21 2018 us=567483 server_bridge_pool_start = 0.0.0.0 Sat Jun 30 20:50:21 2018 us=567489 server_bridge_pool_end = 0.0.0.0 Sat Jun 30 20:50:21 2018 us=567495 ifconfig_pool_defined = DISABLED Sat Jun 30 20:50:21 2018 us=567501 ifconfig_pool_start = 0.0.0.0 Sat Jun 30 20:50:21 2018 us=567508 ifconfig_pool_end = 0.0.0.0 Sat Jun 30 20:50:21 2018 us=567514 ifconfig_pool_netmask = 0.0.0.0 Sat Jun 30 20:50:21 2018 us=567520 ifconfig_pool_persist_filename = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=567526 ifconfig_pool_persist_refresh_freq = 600 Sat Jun 30 20:50:21 2018 us=567532 ifconfig_ipv6_pool_defined = DISABLED Sat Jun 30 20:50:21 2018 us=567538 ifconfig_ipv6_pool_base = :: Sat Jun 30 20:50:21 2018 us=567547 ifconfig_ipv6_pool_netbits = 0 Sat Jun 30 20:50:21 2018 us=567554 n_bcast_buf = 256 Sat Jun 30 20:50:21 2018 us=567560 tcp_queue_limit = 64 Sat Jun 30 20:50:21 2018 us=567565 real_hash_size = 256 Sat Jun 30 20:50:21 2018 us=567571 virtual_hash_size = 256 Sat Jun 30 20:50:21 2018 us=567577 client_connect_script = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=567583 learn_address_script = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=567589 client_disconnect_script = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=567594 client_config_dir = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=567600 ccd_exclusive = DISABLED Sat Jun 30 20:50:21 2018 us=567606 tmp_dir = '/tmp' Sat Jun 30 20:50:21 2018 us=567612 push_ifconfig_defined = DISABLED Sat Jun 30 20:50:21 2018 us=567618 push_ifconfig_local = 0.0.0.0 Sat Jun 30 20:50:21 2018 us=567624 push_ifconfig_remote_netmask = 0.0.0.0 Sat Jun 30 20:50:21 2018 us=567630 push_ifconfig_ipv6_defined = DISABLED Sat Jun 30 20:50:21 2018 us=567636 push_ifconfig_ipv6_local = ::/0 Sat Jun 30 20:50:21 2018 us=567643 push_ifconfig_ipv6_remote = :: Sat Jun 30 20:50:21 2018 us=567649 enable_c2c = DISABLED Sat Jun 30 20:50:21 2018 us=567655 duplicate_cn = DISABLED Sat Jun 30 20:50:21 2018 us=567660 cf_max = 0 Sat Jun 30 20:50:21 2018 us=567666 cf_per = 0 Sat Jun 30 20:50:21 2018 us=567672 max_clients = 1024 Sat Jun 30 20:50:21 2018 us=567678 max_routes_per_client = 256 Sat Jun 30 20:50:21 2018 us=567684 auth_user_pass_verify_script = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=567690 auth_user_pass_verify_script_via_file = DISABLED Sat Jun 30 20:50:21 2018 us=567696 auth_token_generate = DISABLED Sat Jun 30 20:50:21 2018 us=567702 auth_token_lifetime = 0 Sat Jun 30 20:50:21 2018 us=567707 port_share_host = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=567713 port_share_port = '[UNDEF]' Sat Jun 30 20:50:21 2018 us=567719 client = ENABLED Sat Jun 30 20:50:21 2018 us=567725 pull = ENABLED Sat Jun 30 20:50:21 2018 us=567730 auth_user_pass_file = '/etc/openvpn/pass.txt' Sat Jun 30 20:50:21 2018 us=567737 OpenVPN 2.4.6 x86_64-pc-linux-gnu [SSL (OpenSSL)] [LZO] [EPOLL] [MH/PKTINFO] [AEAD] built on Jun 30 2018 Sat Jun 30 20:50:21 2018 us=567749 library versions: OpenSSL 1.0.2o 27 Mar 2018, LZO 2.10 Sat Jun 30 20:50:21 2018 us=568049 WARNING: --ns-cert-type is DEPRECATED. Use --remote-cert-tls instead. Sat Jun 30 20:50:21 2018 us=568071 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts Sat Jun 30 20:50:21 2018 us=568631 LZO compression initializing Sat Jun 30 20:50:21 2018 us=568703 Control Channel MTU parms [ L:1622 D:1212 EF:38 EB:0 ET:0 EL:3 ] Sat Jun 30 20:50:21 2018 us=901910 Data Channel MTU parms [ L:1622 D:1450 EF:122 EB:406 ET:0 EL:3 AF:3/1 ] Sat Jun 30 20:50:21 2018 us=901978 Local Options String (VER=V4): 'V4,dev-type tun,link-mtu 1542,tun-mtu 1500,proto UDPv4,comp-lzo,cipher BF-CBC,auth SHA1,keysize 128,key-method 2,tls-client' Sat Jun 30 20:50:21 2018 us=901988 Expected Remote Options String (VER=V4): 'V4,dev-type tun,link-mtu 1542,tun-mtu 1500,proto UDPv4,comp-lzo,cipher BF-CBC,auth SHA1,keysize 128,key-method 2,tls-server' Sat Jun 30 20:50:21 2018 us=902005 TCP/UDP: Preserving recently used remote address: [AF_INET]172.97.103.52:1194 Sat Jun 30 20:50:21 2018 us=902028 Socket Buffers: R=[212992->212992] S=[212992->212992] Sat Jun 30 20:50:21 2018 us=902038 UDP link local: (not bound) Sat Jun 30 20:50:21 2018 us=902048 UDP link remote: [AF_INET]172.97.103.52:1194 Sat Jun 30 20:50:22 2018 us=190846 TLS: Initial packet from [AF_INET]172.97.103.52:1194, sid=a850029d 5e8d923c Sat Jun 30 20:50:22 2018 us=190980 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this Sat Jun 30 20:50:22 2018 us=487320 VERIFY OK: depth=1, CN=FuntooHost Sat Jun 30 20:50:22 2018 us=487563 VERIFY OK: nsCertType=SERVER Sat Jun 30 20:50:22 2018 us=487577 VERIFY OK: depth=0, CN=FuntooHost Sat Jun 30 20:50:23 2018 us=89113 Control Channel: TLSv1.2, cipher TLSv1/SSLv3 ECDHE-RSA-AES256-GCM-SHA384, 2048 bit RSA Sat Jun 30 20:50:23 2018 us=89193 [FuntooHost] Peer Connection Initiated with [AF_INET]172.97.103.52:1194 Sat Jun 30 20:50:24 2018 us=305228 SENT CONTROL [FuntooHost]: 'PUSH_REQUEST' (status=1) Sat Jun 30 20:50:24 2018 us=595382 PUSH: Received control message: 'PUSH_REPLY,route 10.100.0.1,topology net30,ping 10,ping-restart 120,ifconfig 10.100.0.6 10.100.0.5,peer-id 0,cipher AES-256-GCM' Sat Jun 30 20:50:24 2018 us=595484 OPTIONS IMPORT: timers and/or timeouts modified Sat Jun 30 20:50:24 2018 us=595496 OPTIONS IMPORT: --ifconfig/up options modified Sat Jun 30 20:50:24 2018 us=595504 OPTIONS IMPORT: route options modified Sat Jun 30 20:50:24 2018 us=595512 OPTIONS IMPORT: peer-id set Sat Jun 30 20:50:24 2018 us=595521 OPTIONS IMPORT: adjusting link_mtu to 1625 Sat Jun 30 20:50:24 2018 us=595529 OPTIONS IMPORT: data channel crypto options modified Sat Jun 30 20:50:24 2018 us=595539 Data Channel: using negotiated cipher 'AES-256-GCM' Sat Jun 30 20:50:24 2018 us=595556 Data Channel MTU parms [ L:1553 D:1450 EF:53 EB:406 ET:0 EL:3 AF:3/1 ] Sat Jun 30 20:50:24 2018 us=595651 Outgoing Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key Sat Jun 30 20:50:24 2018 us=595663 Incoming Data Channel: Cipher 'AES-256-GCM' initialized with 256 bit key Sat Jun 30 20:50:24 2018 us=595797 ROUTE_GATEWAY 192.168.0.1/255.255.255.0 IFACE=wlan0 HWADDR=9c:2a:70:89:91:e9 Sat Jun 30 20:50:24 2018 us=596050 TUN/TAP device tun0 opened Sat Jun 30 20:50:24 2018 us=596083 TUN/TAP TX queue length set to 100 Sat Jun 30 20:50:24 2018 us=596100 do_ifconfig, tt->did_ifconfig_ipv6_setup=0 Sat Jun 30 20:50:24 2018 us=596117 /bin/ifconfig tun0 10.100.0.6 pointopoint 10.100.0.5 mtu 1500 Sat Jun 30 20:50:24 2018 us=601965 /etc/openvpn/up.sh tun0 1500 1553 10.100.0.6 10.100.0.5 init Sat Jun 30 20:50:24 2018 us=676540 /bin/route add -net 10.100.0.1 netmask 255.255.255.255 gw 10.100.0.5 Sat Jun 30 20:50:24 2018 us=677323 Initialization Sequence Completed
Servidor Dante Proxy (sock5)
Inicie o Dante proxy e adicione ao boot:
root # /etc/init.d/dante-sockd start root # rc-update add dante-sockd
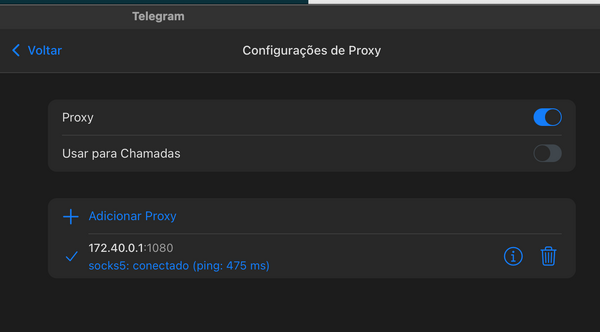
Cliente sock5
Abra o aplicativo e utilize o ip do TUN do servidor, exemplo 172.40.0.1 e porta 1080: